The Security Model
EVA Netmodeler has a comprehensive security model. This is necessary since EVA Netmodeler may be used in environments where a great deal of sensitive information is held. This may pertain to corporate strategy, personnel
evaluations, or patient histories. The model has been designed to be very flexible, but at the same time relatively easy to administer.
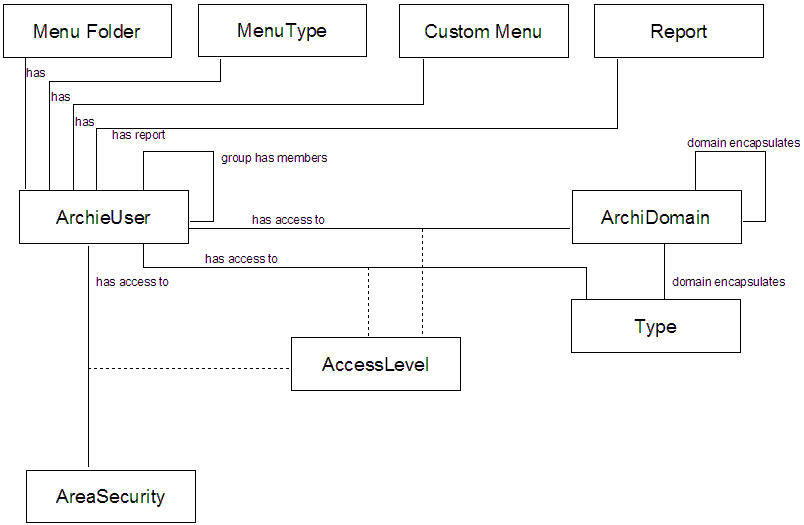
The EVA Netmodeler security meta model
Archi Users
An individual with a password to sign on and use the EVA Netmodeler tool is an ArchiUser. A user can belong to none,
one or more User Groups. Where rights are assigned to a group, all users in that group will have the relevant rights. A
user can belong to several groups, thereby acquiring the rights of all the groups of which he/she is a member.
User Groups
A User Groups is simply an ArchiUser that is related to other ArchiUsers via the "group has members" relationship. Users are assigned to groups by:
- Creating an ArchiUser for the group
- Assigning the desired privileges to this user;
- Creating an ArchiUser for each of the group members, but not assigning any privileges to these
- Linking the users to the group via the "Group has members / is member of group" relationship.
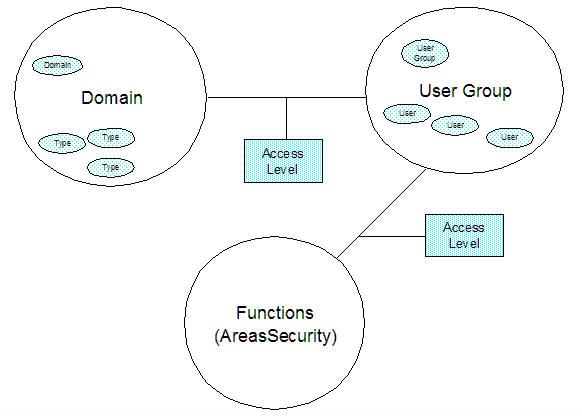
Area Security
Area security is a concept that allows us to control what functions (e.g. browsers, utilities, custom views etc.) within the
tool a user or group may access. This would allow us to exclude users from maintaining types, for example, using the Type Browser. Each major functional area of the tool has an associated Area Security item.
Access Level
Access Level items are info nodes which reflect the access privileges of a user or group to a type, default item, or
instances of the type (items). Each entry has five or less access privilege codes, with assigned meanings as follows:
C = Create - user is allowed to create items of this type
V = View - user may view items of this type
U = Update - user may edit and change items of this type
D = Delete - user may delete items of this type
T = Template - user may modify templates associated with this item
Access Levels are used to control access at three different levels:
Meta - Permissions related to working with the type definition
Default - Permissions related to working with the default node for the type
Instance - Permissions related to instances (items) of the type
If the relevant access privilege code is present in the correct access level of the Access Level node linking a user (or
group) to the type in question, then the action can be performed. For example if we are dealing with an Access Level node that looks like this:
then the user could (provided they have the appropriate Area Security privileges for the required browsers):
View the meta data (the type definition in the Type Browser)
View and Update the Default item for the type
Create, View, Update, Delete and work with templates for the items of the type
ArchiDomain
A domain within EVA Netmodeler is a set of related types. They are usually used to make management of the environment and the
knowledge base as well as user permissions and security easier. The Inspired Architecture Frameworks, when installed, also make use of domains to group the various parts of the meta model into logical sets.
A domain encapsulates one or more types. Types can belong to multiple domains. Domains can contain other domains. If a user or
user group is granted rights to a domain, these permissions are assumed to apply to all types within the domain, unless overridden.
Filters can be used to allow the user to focus on a subset of the domains available. All types not in selected active domains will be hidden.
Domains can also be useful in selecting subsets of the meta model or knowledge base to export.
Menu Folder, Menu Type, Custom Menu and Report
These types are contain shortcuts used to provide quick access to user generated folders and menus. By default, a
relationship is automatically created from the ArchiUser that creates one of these items to the item. The item may be
exposed to other ArchiUsers by manually creating the same type of relationship from the user to the relevant item. Note
that this is not strictly access control but rather a way to build and manage shortcuts for users. Any user will be able to access the list of items of these types via one of the EVA Netmodeler
browsers and relate it to any other user.
Managing Security with Domains and Groups
The simplest model for user rights administration is to:
- Use domains to group types into logical sets
- Use User Groups to group individual users into roles
- Allocate privileges with respect to access/update etc between the user groups and the domains
Instance level update access control
The Archi2UpdatedBy provides instance level access to users. When an item is created containing a property of this
type, the value is set to the user id of the user who created it. When the same item is edited, a drop-down box is
displayed containing a list of all user ids. As soon as a user id is selected, only that user will have edit access to to that instance. However, the user has to have edit access to the type at the meta level as well.
Anonymous Access
The Anonymous Access feature allows unnamed users to access data in the repository via
- Composite Views
- Reports
- Generic Update Display and Edit (GIDE)
- Custom Views
Anonymous access enables you to embed EVA Netmodeler content in web sites and capture information into the EVA Netmodeler repository from web forms without the need for the web users to log on the EVA Netmodeler. This enables
users to query EVA Netmodeler in realtime without logging in, which is particularly useful for public sites or corporate intranets
Access is gained via special URL's which can be embedded in other web pages using the standard HREF tag. Anonymous Access can also be used to create sessions that do not time-out for in-house users. Refer to the Anonymous Access section for information on how to configure anonymous access.
Effective Rights
EVA Netmodeler filters all information rendered to a user using the security settings. Any functions, items, actions etc.
that are not permitted are simply not shown to the user. I.e. if a user does not have rights to use a certain browser or
function, it will not appear on a toolbar and/or associated buttons will not be present. If a user may not see certain types,
they will not appear in any lists presented to the user. If a user may not see defaults for a type, they will not appear in the instance lists, and so on.
Conceptual View of Users and Domains, Functional Security
Timing
Security information can be altered at any time by an authorised user. Settings for a user are read at log on time and will
remain in force for the duration of that session. If you want to change rights for a logged on user, they may be altered,
but the user will have to log out and log in again to see the changed rights. Alternatively the user can use the Refresh User Security utility to reload security rights for a user without logging off and back on again.
Sessions
A new session is started each time a user logs in to EVA Netmodeler successfully. If EVA Netmodeler detects long
inactivity for a user, the session will expire (this is to preserve security when users do not log out, but leave their browser
open and logged on). If the session has expired and further activity is attempted, the user is informed that the session
has expired and a new log on is required. The immediate effect will sometimes be that all functions and lists in the browser are blank - this occurs because EVA Netmodeler
filters the information provided by what is permitted by the access rights, which is nothing if the session has expired!
User Permissions Report
It can be quite difficult to determine exactly what permissions a user will have once all the above are resolved. The User Access Permissions report provides an easy way to list the net set of permissions that a user (or all users) will have
after all inheritance, relationships etc. are resolved.
|